Criminological Explanations of Cybercrime
Module 3 provides an overview of criminological theories that explain the causes of crime. It categorizes various theories into major groups, such as biological, psychological, sociological, and contemporary approaches, and outlines the foundational assumptions behind each. Understanding these assumptions is essential, as they shape the perspectives on why crime occurs and how society should respond. This module also emphasizes the importance of theory in understanding crime causation. Theories not only offer explanations but also influence public policy decisions and practices in both the private and public sectors. By explaining the link between theory and policy, the chapter highlights how theoretical perspectives can guide law enforcement strategies, crime prevention efforts, and rehabilitation programs. In addition, there is a focus on the relationship between criminology and Cybercriminology, discussing how both fields share similarities in studying crime while differing in focus areas. Criminology traditionally examines crime within physical spaces, whereas Cybercriminology focuses on digital and cyber environments. In summary, by the end of this chapter, students will gain a comprehensive understanding of the various criminological theories, their applications in policymaking, and the evolving field of Cybercriminology.
Learning Objectives
After completing this module, you should be able to:
- Identify and describe the main categories of criminological theories, including biological, psychological, sociological, and contemporary approaches.
- Explain the core assumptions of each theoretical perspective and how they influence understandings of crime causation.
- Analyze how criminological theories shape policy, including their impact on law enforcement strategies, crime prevention, and rehabilitation initiatives.
- Differentiate between criminology and cybercriminology, highlighting their common focus on crime and their unique areas of study (physical versus digital environments).
- Apply theoretical frameworks to examples of both traditional and cybercrime.
- Examine real-world cases and resources (readings, talks, videos, and podcasts) to understand how theory relates to practice in explaining and solving crime.
- Explore career pathways in criminology and cybercriminology, and understand how theory underpins professional practice in these fields.
A key theme of this module is the connection between criminology and cybercriminology. While criminology usually studies crime in physical spaces, cybercriminology uses similar theories to analyze digital environments, focusing on how human behavior, social structures, and technology come together in cyberspace. This link shows both the ongoing similarities and the new challenges introduced by cybercrime.
Through the assigned readings, videos, and podcasts, students will deepen their understanding of how theoretical frameworks relate to real-world issues and careers in the field. For example, Karuppannan (2018) explores the development of cybercriminology, Anderson (2017) emphasizes the role of human behavior in cybercrime, and THV11 (2012) traces how investigations evolve with technology. Additional resources from Khan Academy and TEDx Talks offer accessible overviews of rational choice, behavioral, and social theories, while podcasts like “Cybercrimeology” expose students to current debates and practitioner insights.
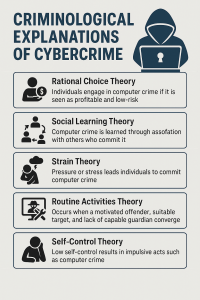
Cybercrime, also called computer crime, involves illegal activities performed using computers or digital technology. Criminologists have developed different theories to explain why people engage in such behavior.
- Rational Choice Theory – Offenders assess potential rewards and risks, viewing cybercrime as lucrative and with relatively low dangers.
- Social Learning Theory – People acquire cybercriminal skills and attitudes by observing their peers, online groups, or media portrayals of hackers.
- Strain Theory – Social or economic pressures can drive individuals toward cybercrime as a way to relieve frustration or gain status.
- Routine Activities Theory states that cybercrime happens when motivated offenders find vulnerable digital targets lacking proper guardianship (e.g., weak cybersecurity).
- Self-Control Theory – Low self-control and impulsivity increase the likelihood of committing cybercrime.
 While traditional criminology focuses on crimes in physical locations, cybercriminology adapts these frameworks to the digital world, where crime crosses borders and advances with technology. Analyzing cybercrime through theoretical lenses is essential because theories inform policy, prevention efforts, law enforcement techniques, and rehabilitation programs.
While traditional criminology focuses on crimes in physical locations, cybercriminology adapts these frameworks to the digital world, where crime crosses borders and advances with technology. Analyzing cybercrime through theoretical lenses is essential because theories inform policy, prevention efforts, law enforcement techniques, and rehabilitation programs.
Cybercriminology is becoming increasingly vital because of rising cybercrime rates, significant economic losses, global scope, privacy and data concerns, and the need for international cooperation. It also helps develop skilled cybersecurity professionals, raises public awareness, and guides laws and regulations to combat complex digital crimes.
In summary, this module highlights that understanding theory is crucial to understanding cybercrime: theories explain behavior, influence responses, and link criminology to real-world practice in both traditional and digital settings.
Key Takeaways
Key Terms/Concepts
Applied Criminology
Behavioral Theory
Biological Theories
Classical School of Criminology
Contemporary Theories
Correlation
Crime Causation
Crime Prevention
Criminal Justice
Criminologist
Criminology
Cybercrime
Cybercriminology
Cyberspace
Cybervictims
Determinism
Positivism
Psychological Theories
Public Policy Connection
Rational Choice
Routine Activities Theory
Social Theory
Sociological Theories
Space Transition Theory
Theoretical Criminology
Theory
Theory-to-Practice Link
Modern Example
An excellent resource containing discussions on Cybercriminology that advance the field and emphasize the importance of criminology in examining and responding to all forms of digital crime.
“Cybercrimeology is a podcast about cybercrime, its research and its researchers. We talk to top researchers from around the world to learn about different forms of cybercrime and their research. We learn about cybercrime theory, organized crime online, Darknet drug markets, cybercrime awareness and crime prevention, technology-facilitated intimate partner violence and much more. The podcast has been running since November of 2019 and there is still so much to learn. I am happy to have you along for the journey into this fascinating subject” (Cybercriminology, 2024) [last accessed, February 2024].
Access the “Cybercrimeology” podcast by clicking HERE
Read, Review, Watch and Listen
- Read Cyber Criminology: Evolution, Contribution and Impact (Karuppannan, 2018) [click Download file PDF] (pp. 1-16)
- Key Terms: Cybercriminology, Cybercrime, Theory-to-Practice Link.
- Shows how criminological theories adapt to the digital age and how cybercrime challenges traditional frameworks.
- Review TEDx Talks Cyber Crime Isn’t About Computers: It’s About Behavior (Anderson, 2017) [also embedded below]
- Key Terms: Behavioral Theory, Psychological Theories, Cybercrime.
- Highlights the role of human behavior and decision-making in cybercrime.
- Watch How criminal investigations have evolved along with technology (THV11, 2012) [also embedded below / last accessed February 2024]
- Key Terms: Crime Prevention, Public Policy Connection, Cybercrime.
- Demonstrates the impact of technological change on law enforcement practices.
- Watch Careers in criminology (UniSC University of the Sunshine Coast, Aug. 30, 2021) [also embedded below]
- Key Terms: Criminology, Cybercriminology, Rehabilitation, Crime Prevention.
- Connects theory to practice and professional opportunities.
- Watch Kahan Academy’s Rational Choice-Exchange Theory (Brown, S. 2014)
- Key Terms: Rational Choice Theory, Contemporary Theories.
- Explains decision-making models of crime causation.
- Watch Kahan Academy’s Behavioral Theory (Desai, 2019)
- Key Terms: Behavioral Theory, Psychological Theories.
- Outlines conditioning and learned behavior explanations of crime.
- Watch Social Theories Overview (Brown, 2015)
- Key Terms: Sociological Theories, Social Theories, Crime Causation.
- Provides broad context on social structure and group influences on crime.
- Watch Social Theories Overview (part 2) (Brown, 2015)
- Key Terms: Sociological Theories, Social Theories, Crime Causation.
- Provides broad context on social structure and group influences on crime.
- Listen to Cybercrimeology most recent episode and voluntarily explore others (last accessed February 2024)
- Key Terms: Cybercriminology, Public Policy Connection, Theory-to-Practice Link.
- Offers practitioner insights and current issues in the field.
Activity 3 – Criminological Explanations of Cybercrime
STOP!!
Students should review the course syllabus to determine the assignment of this activity.
This is a copy of the module’s activity that students find within Blackboard. For that reason, refer to the Activities page to submit your work for review.
Purpose
The purpose of this activity is to introduce traditional theories of crime causation that serve as the basis of examining social phenomena.
Overview
Within the framework of classical/choice theory, perceptions of opportunities to commit crime are very important. Routine activities theory builds on this foundation by claiming that crimes are more likely to be committed by motivated offenders who have suitable targets in the absence of capable guardians. Routine activities of perpetrators, as well as those of potential victims and other actors, thus result in opportunities for committing and preventing cybercrimes with technology. As such, routine activities theory has important implications for understanding crimes committed with or prevented with computers, other electronic IT devices, or information systems.
One measure of situational crime prevention is target hardening. Target hardening makes it more difficult or increases the amount of effort needed for offenders to carry out crimes on specific targets. The use of locked doors, windows, alarm systems, watchdogs, and community crime watch programs are all examples of target hardening–making it harder to become a victim of crime.
Instructions
- Locate a computer crime or IT-enabled abuse news story using a search engine of your choice, e.g., Google, or an electronic COD library resource.
- Review the tenets of routine activities theory (RAT) as introduced within Chapter 3 (see pp. 50-51)
- Watch Cybercrime isn’t about computers” It’s about behavior by Adam Anderson
- As a byproduct of rational choice theory (i.e., routine activities), review Arizona State University Center for Problem-Oriented Policing’s Twenty-Five Techniques of Situational Prevention (University, 2021)
User: n/a – Added: 5/17/17
Answer the following questions
- Consider the example of crime you identified and explain how it could have been prevented. Include techniques of situational prevention in your explanation.
- In your own words, explain how technology, particularly cyberspace, has changed behavior (if at all), and describe what methods of reducing opportunity are necessary to decrease the prevalence of cybercrime.
AND Answer one of the following three questions:
- Use rational choice exchange theory to explain “Why?” cybercrime occurs.
- Use behavioral theory to explain “Why?” cybercrime occurs.
- Use social theory to explain “Why?” cybercrime occurs.
Key Terms/Concepts
Behavioral theory, or behaviorism, is the second major psychological theory. It holds that human behavior is learned through experiences. The key idea of behavioral theory is that people change their behavior based on how others react to it (Bandura, 1978).
Cybercriminology merges coursework in Criminal Justice and Computer Science to examine the increasing issue of computer crime.
Rational choice in criminology is based on a utilitarian view that humans are reasoning actors who consider means and ends, costs and benefits, to make rational decisions. This approach was developed by Cornish and Clarke to help understand situational crime prevention.
Routine Activities Theory – According to Cohen and Felson, crime happens when three factors come together in time and space: (1) a motivated offender, (2) a suitable target, and (3) the absence of a capable guardian, such as inadequate software protection.
Social theory is an empirically validated set of ideas within the social sciences, such as social processes, that sees criminality as a result of people’s interactions with various organizations, institutions, and social processes. People from all walks of life can become criminals if they maintain destructive social relationships.
Theory is an effort to answer the question of “Why?” within the framework of established propositions that form the basis for empirical examination.
Refer to the course learning management system (LMS), Blackboard (BB), for the correct due date. Also, submit your work through BB for grading.
Supplemental Resources
- On-line Activities Guardianship and Malware Infection-An Examination of Routine Activities Theory (A. Bossler & T. Hold, 2009 International Journal of Cyber Criminology (IJCC) ISSN: 0974 – 2891 January – June 2009, Vol 3 (1): 400–420.
- International Journal of Cybercriminology (last accessed, February 2024)
- Specialize in Cyber Criminology at UQ – UQ Humanities, Arts and Social Sciences (last accessed, February 2024)
- Enhancing relationships between criminology and cybersecurity (Dupont, Benoit & Whelan, Chad. (2021). Enhancing relationships between criminology and cybersecurity. Journal of Criminology. 54. 000486582110039. 10.1177/00048658211003925.)
Read, Review, Watch and Listen to all listed materials by the due date listed within the course LMS site.
Click HERE to report any needed updates, e.g., broken links.
A multidisciplinary field that utilizes theories, research methods, and practical knowledge to address and solve real-world problems related to crime, criminal behavior, and the criminal justice system. It involves the practical application of criminological theories and concepts to develop strategies and interventions that can prevent crime, reduce criminal behavior, and improve the functioning of the criminal justice system.
Applied criminology draws from various disciplines such as sociology, psychology, law, anthropology, and public policy. Its primary focus is on practical outcomes and the implementation of evidence-based practices to create safer communities, enhance the effectiveness of law enforcement agencies, and promote social justice.
Professionals working in applied criminology may engage in a range of activities, including conducting research to evaluate the effectiveness of crime prevention programs, analyzing crime patterns and trends, developing policies and interventions to address specific crime issues, providing expertise and guidance to law enforcement agencies, advocating for criminal justice reform, and working with communities to implement crime prevention strategies.
Overall, applied criminology aims to bridge the gap between theoretical knowledge and real-world application, with the goal of reducing crime, improving the criminal justice system, and creating safer societies.
Also known as behaviorism is the second major psychological theory. This theory maintains that human behavior is developed through learning experiences. The hallmark of behavioral theory is the notion that people alter or change their behavior according to the reactions this behavior elicits in other people (Bandura, 1978).
Explanations of crime that emphasize genetic, neurological, or physiological factors as influences on criminal behavior.
A theory of crime and punishment that originated in the 18th century and was developed by various Enlightenment thinkers, most notably Cesare Beccaria and Jeremy Bentham. It is considered one of the foundational theories of criminology. The classical school of criminology is based on the idea of free will and rational choice. It posits that individuals are rational beings who weigh the potential benefits and costs of their actions before engaging in criminal behavior. According to this perspective, people choose to commit crimes when the perceived benefits outweigh the potential risks or punishments.
More recent approaches that build on or revise earlier explanations, including rational choice, social learning, and integrated theories.
Refers to a statistical measure that quantifies the relationship or association between two or more variables. It describes the extent to which changes in one variable are related to changes in another variable. Correlation does not imply causation, meaning that a correlation between two variables does not necessarily indicate that one variable causes the other to change. Correlation analysis is widely used in various fields, including statistics, social sciences, economics, and medical research. It helps researchers and analysts understand the degree and direction of association between variables, identify patterns, make predictions, and guide decision-making. However, it is important to note that correlation alone does not establish a cause-and-effect relationship between variables, as other factors or variables may be involved.
The study of the underlying reasons why individuals or groups commit crimes.
Strategies and programs designed to reduce crime before it occurs, often shaped by criminological theory.
Refers to the system of practices and institutions established by governments to maintain social order, deter, and control crime, and administer justice to those who violate the law. It encompasses a broad range of processes, organizations, and individuals involved in the detection, investigation, prosecution, and punishment of criminal offenses.
A professional who studies the causes, consequences, prevention, and control of criminal behavior. Criminology is a multidisciplinary field that draws from various disciplines, including sociology, psychology, law, anthropology, and criminal justice. Criminologists apply scientific methods and theories to analyze and understand crime patterns, criminal behavior, and the functioning of the criminal justice system.
The work of a criminologist can vary depending on their specialization and the context in which they operate. Some common roles and responsibilities of criminologists include:
1. Criminologists conduct empirical research to examine crime trends, identify risk factors for criminal behavior, and evaluate the effectiveness of crime prevention programs and policies. They collect and analyze data, design research studies, and interpret findings to contribute to the knowledge and understanding of crime and its implications.
2. Criminologists develop and assess strategies and interventions aimed at preventing crime and reducing recidivism. They work with communities, law enforcement agencies, policymakers, and other stakeholders to implement evidence-based practices and policies that promote public safety and crime reduction.
3. Criminologists analyze existing laws, policies, and practices within the criminal justice system to assess their impact and effectiveness. They provide recommendations for policy reform and improvements based on their research findings and understanding of criminological theories.
4. Some criminologists specialize in the field of criminal profiling, where they use psychological and behavioral analysis to create profiles of unknown criminals based on crime scene evidence and patterns. They assist law enforcement agencies in investigations by providing insights into the likely characteristics and motivations of offenders.
5. Criminologists often work in academic institutions, teaching criminology courses and mentoring students. They contribute to the education and training of future professionals in the field of criminal justice. Additionally, criminologists may engage in public outreach and advocacy, promoting evidence-based policies and raising awareness about criminal justice issues.
Overall, criminologists play a crucial role in understanding, analyzing, and addressing issues related to crime, criminal behavior, and the criminal justice system. Their work aims to inform policy, improve crime prevention strategies, and contribute to the development of effective and fair criminal justice practices.
The scientific study of crime, criminal behavior, and the criminal justice system, traditionally focused on crime in physical spaces.
Is any criminal offense (e.g., fraud, theft, or distribution of child sexual abuse material [CSAM]) committed using a computer specially to access without authorization, transmit, or manipulate data via the Internet or otherwise aided by various forms of computer technology, such as the use of online social networks to bully others or sending sexually explicit digital photos with a smart phone.
Combines coursework within the behavioral sciences and Computer Science to study the growing problem of computer crime.
The virtual environment created by interconnected computers and networks, where information and communication take place.
The individuals or groups who suffer harm or loss as a result of cyber crimes, such as identity theft, cyber bullying, online fraud, etc.
A philosophical concept that posits that every event or phenomenon, including human actions and choices, is causally determined by preceding events and conditions. It suggests that there is a fixed chain of cause and effect in the universe, and given the same circumstances, the same outcome will always occur.
According to determinism, free will is an illusion, and human behavior is ultimately governed by factors beyond individual control, such as genetics, environment, upbringing, and societal influences. It suggests that individuals do not have true autonomy or the ability to make choices that are independent of causal factors.
Within criminology refers to a theoretical approach that emphasizes the application of scientific methods and empirical observation in the study of crime and criminal behavior. It emerged in the late 19th century as a response to the limitations of earlier philosophical and moralistic explanations of crime.
Approaches that focus on individual mental processes, personality traits, and behavioral conditioning as causes of crime.
The way theories of crime influence government decisions, laws, law enforcement strategies, prevention efforts, and rehabilitation practices.
In criminology adopts a utilitarian belief that humans are reasoning actors who weigh means and ends, costs and benefits, in order to make a rational choice. This method was designed by Cornish and Clarke to assist in thinking about situational crime prevention.
According to Cohen and Felson, crime occurs when there is a convergence in time and space of three factors: (1) motivated offender, (2) suitable target, and (3) the absence of a capable guardian, e.g., inadequate software protection.
Is an empirically tested set of ideas within the social sciences, e.g., social process, that views criminality as a function of people's interactions with various organizations, institutions, and processes in society; people in all walks of life have the potential to become criminals if they maintain destructive social relationships.
Perspectives that examine social structures, relationships, and environments (e.g., family, peers, community, inequality) as key influences on criminal behavior.
A theoretical framework proposed by Jaishankar in 2008 to explain the causation of cyber crimes. It argues that people behave differently when they move from one space to another, such as from physical space to cyber space.
Refers to the study of crime and criminal behavior through the lens of various theoretical perspectives. It seeks to understand the causes, patterns, and dynamics of crime by developing and applying theoretical frameworks. Theoretical criminology plays a crucial role in shaping our understanding of crime, informing policy and interventions, and guiding research in the field of criminology.
Theoretical criminology encompasses a wide range of perspectives and theories, each offering different explanations and insights into criminal behavior.
An attempt to answer the question of "Why?" within the framework of established propositions that provide the basis for an empirical examination.
The process of applying theoretical perspectives to real-world cases, investigations, and prevention strategies.


